

- By ACI
- 03 December, 2025
- 10 min Read
Building a Secure Healthcare IT Ecosystem
Healthcare organizations rely on technology to manage patient care, clinical workflows, and administrative work. As digital systems expand, the need for secure Healthcare IT solutions becomes essential for protecting sensitive information and ensuring smooth operations. A secure healthcare IT ecosystem supports HIPAA compliant software, strong data protection practices, and integrated workflows that help teams work together without risk or disruption.
Healthcare decision makers now look for systems that not only protect patient information but also connect front desk staff, billing teams, doctors, nurses, and medical authorities in one environment. A well-designed ecosystem makes this possible through secure EHR integration, identity and access controls, risk assessments, and reliable cloud data security. Aryabh Consulting helps healthcare organizations build systems that follow industry regulations and support daily operations with confidence.
Understanding a Secure Healthcare IT Ecosystem
A secure healthcare IT ecosystem is a connected environment where all digital tools and patient-facing systems work safely as one. It includes clinical applications, administrative software, communication tools, data storage systems, and integration layers that move information between them. Each part must follow strong security practices and meet HIPAA guidelines.
The goal is simple. Protect patient data, ensure compliance, and allow staff to work without technical barriers. This requires secure workflows, controlled access, and consistent monitoring across every system involved in care delivery.
Current Security Challenges for Healthcare Organizations
Healthcare organizations face a growing number of threats that impact patient safety and financial stability.
Common challenges include:
Exposure of PHI stored in outdated systems
Legacy systems hold sensitive information but lack modern controls.
Ransomware attacks that disrupt hospital operations
Attackers target healthcare because data is valuable and downtime is costly.
Lack of strong IAM controls
Weak access rules allow unauthorized entry into patient records.
Gaps in EHR integration and data sharing
Unsecured integration points create risks during data exchange.
Cloud misconfigurations
Systems moved to the cloud without proper governance may expose patient information.
Compliance pressure
Hospitals must maintain HIPAA requirements and follow FDA software compliance guidelines when working with clinical systems.
These challenges show why healthcare data security must be part of every workflow, integration, and decision.
Core Components of a Secure Healthcare IT Ecosystem
Creating a secure environment requires attention to several critical areas. Each part contributes to safe workflows and reduced risk.
1. Cybersecurity Foundation
Every healthcare organization needs strong cybersecurity practices to protect networks, devices, and sensitive data.
Key elements include:
- Continuous monitoring of internal and external systems
- Secure network architecture
- Endpoint protection for computers, tablets, and medical devices
- Threat detection tools that flag unusual activities
- Logging of all system interactions
- Staff training that prevents avoidable risks
A strong cybersecurity foundation supports the rest of the organization and prevents unauthorized access.
2. HIPAA and FDA Compliance
HIPAA compliant software is a requirement for any system that handles PHI. A secure ecosystem uses technical safeguards that support this compliance.
Important components include:
- Access control rules
- Audit trails that record user actions
- Encryption of data at rest and in transit
- Secure login mechanisms
- Policies for retention, deletion, and data availability
- Privacy rules that align with HIPAA standards
Some clinical applications must also follow FDA software compliance depending on their role in patient care. A structured compliance workflow helps organizations meet these guidelines without slowing down operations.
3. Healthcare Data Security in Cloud Environments
Cloud platforms support scalability and faster data access, but they must be configured correctly.
Cloud data security includes:
- Encrypted data storage
- Secure backup and disaster recovery mechanisms
- Proper access governance
- Monitoring tools that track real-time activity
- Controlled sharing of data between departments
- PStrong API protection for EHR integration
A secure cloud environment allows healthcare organizations to improve performance without compromising sensitive information.
4. Identity and Access Management (IAM)
Clear access rules protect patient records and ensure that only authorized users can view or change information.
IAM in healthcare involves:
- Role-based access for front desk teams, billing staff, nurses, doctors, and administrators
- Multi-factor authentication
- Privileged access rules for sensitive operations
- Automated de-provisioning when staff leaves or changes roles
- Session management and access logs
Strong IAM practices reduce insider threats and prevent unauthorized access, which is one of the most common causes of healthcare data breaches.
5. Risk Assessments and Ongoing Security Checks
A secure ecosystem requires regular evaluation. Risk assessments identify vulnerabilities and help organizations maintain a strong security posture.
These assessments review:
- Application security
- Infrastructure gaps
- Compliance practices
- Vendor systems
- Data integration connections
- Cloud configurations
- User access patterns
Routine checks make it easier to find risks early and take corrective action before a threat becomes a serious issue.
Supporting Technologies That Strengthen Security
Modern healthcare systems depend on practical technology that supports security and improves operational performance.
Examples include:
- Python-based tools that monitor system activity and automate alert management
- Blockchain-based audit trails that maintain the integrity of patient records
- Secure APIs for smooth EHR integration
- Cloud infrastructure that supports scalability
- Encryption frameworks for safe data movement
- Interoperability layers that follow HL7 and FHIR standards
These technologies help healthcare organizations operate safely while improving care delivery.
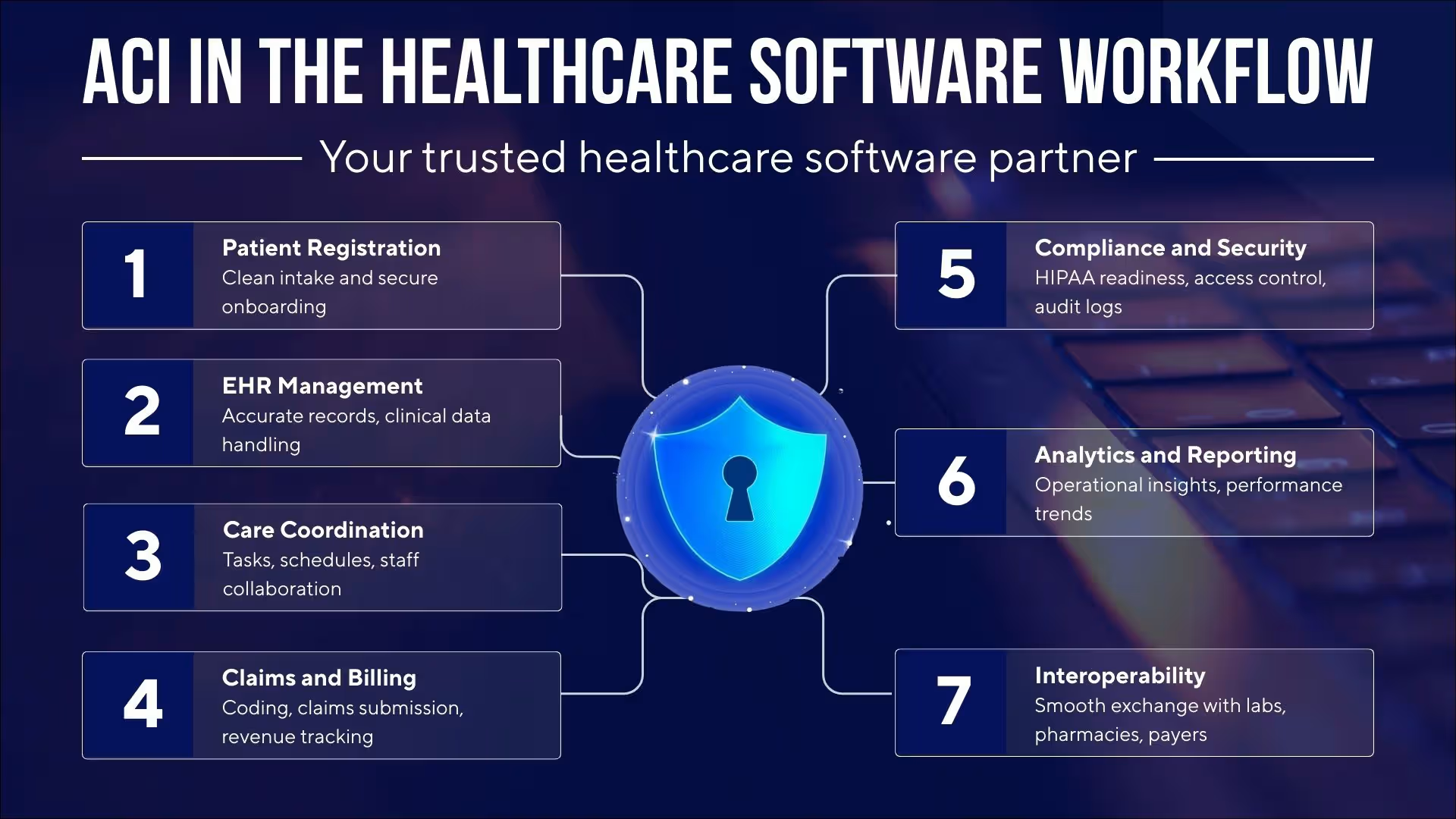
Connecting Every Part of the Healthcare Workflow
A strong healthcare IT ecosystem is not only secure. It is also connected. Every department in a healthcare facility depends on reliable access to accurate information. A disconnected workflow creates delays, errors, and inconsistent patient experiences.
Custom software designed by Aryabh Consulting allows organizations to centralize key processes in one secure environment.
Connection Between Departments
- The front desk manages patient registration, appointment scheduling, and document collection
- Doctors and nurses view patient history, lab results, prescriptions, and clinical notes
- Billing teams track claims, insurance verification, and payment status
- Medical authorities handle compliance approvals and internal reviews
- Administrators manage reporting, analytics, and operational oversight
This connection improves communication and reduces manual work.
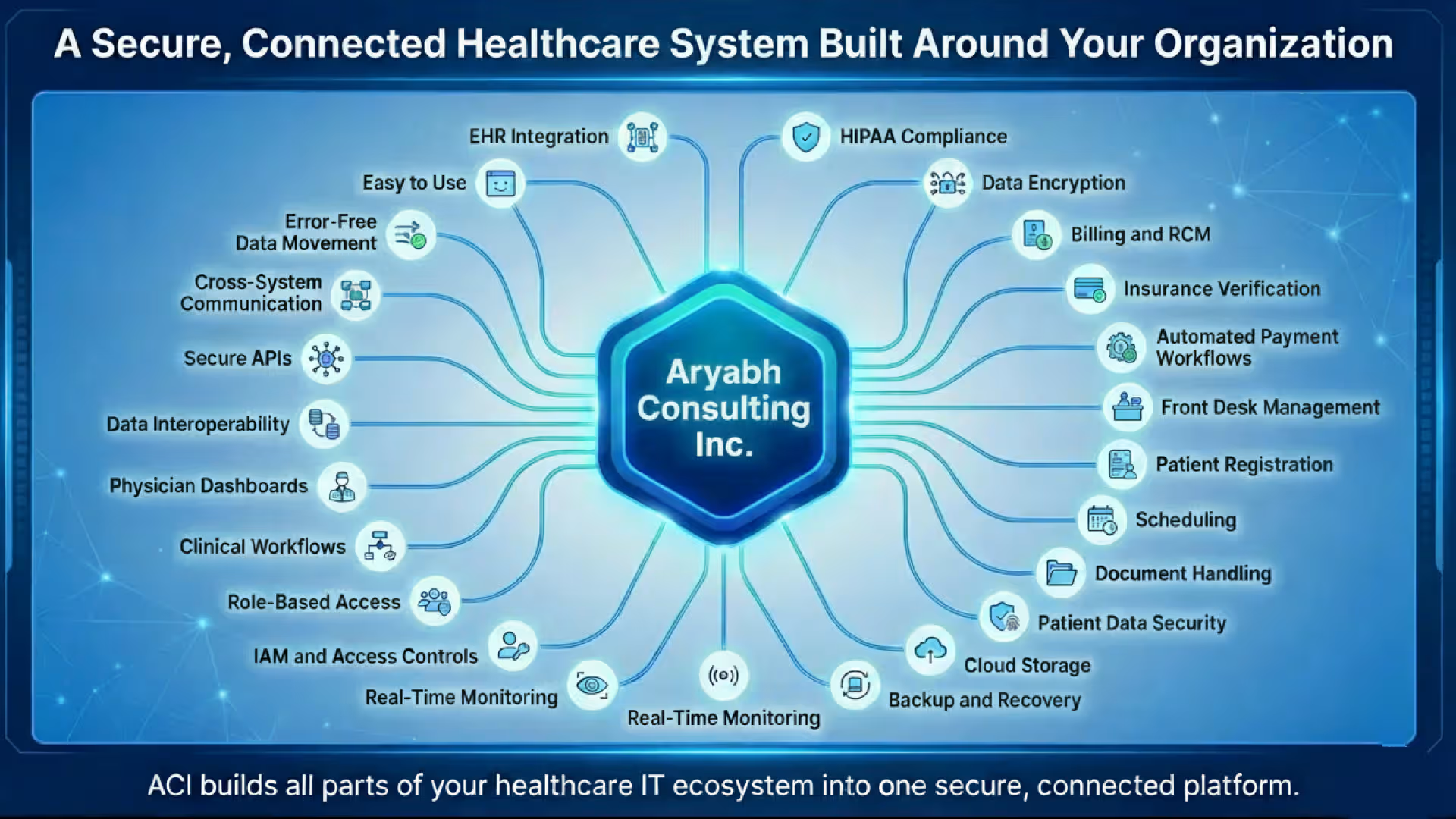
How One Integrated System Supports Secure Patient Workflows
Aryabh Consulting builds custom healthcare IT solutions that connect every department through secure workflows. The platform is designed around user needs and follows patients data security standards.
Key advantages include:
1. Centralized patient information
All data stays in one secure location with cloud data security controls.
2. Accurate and fast billing
Billing teams work with updated data from patient visits, reducing errors.
3. Controlled access
IAM ensures each staff member sees only what they need.
4. Safe EHR integration
Clinical data moves securely between systems.
5. HIPAA compliant handling of all data
Every action is recorded with protected audit trails.
6. Better communication among staff
Front desk teams, doctors, nurses, and billing departments share real-time information.
7. Automated workflows
Routine tasks move through the system without manual processing.
8. Secure patient engagement
Appointments, forms, notifications, and document access follow strict security rules.
This approach gives healthcare organizations a complete view of their operations and reduces safety and compliance risks.
The Role of Healthcare Consulting in Building Secure Systems
Healthcare organizations often manage complex workflows. A consulting partner helps evaluate current systems, identify gaps, and design a secure roadmap. Aryabh Consulting works with healthcare teams to understand their needs and build scalable business solutions that reduce risk.
Consulting support includes:
- Workflow evaluation
- Custom architecture design
- EHR integration strategy
- Data security review
- Compliance planning
- Cloud migration support
- Infrastructure modernization
- Operational optimization
This approach ensures that technology supports clinical and administrative teams without adding complexity.
Frequently Asked Question
1. Why is a secure healthcare IT ecosystem important for patient care?
It protects sensitive information and ensures that staff work with accurate and updated data.
2. How does IAM improve healthcare data security?
It restricts access based on job roles so only authorized users can view or change patient information.
3. Can cloud systems support HIPAA compliant software?
Yes. Cloud environments can be configured with encryption, access control, and monitoring that match HIPAA standards.
4. Why are risk assessments needed?
They help identify vulnerabilities before they impact operations.
5. Is EHR integration safe?
With secure APIs, encryption, and proper access rules, EHR data can move safely between systems.

